EN - eLearning - EC-Council Certified Encryption Specialist (ECES) v3
Elevate your data security with cryptographic and quantum practices
Download Brochure
If you want to learn more about the training, check out the official training brochure!
What you'll get
- One (1) Year Access to the e-courseware.
- Six (6) months access to EC-Council's official online lab environment.
- Certification or Exam voucher valid for a period of one (1) year.
- Certification and examination fees are included in the price of the training course.
- Expert instructor-led training modules with streaming video presentations and learning supplements for an all-inclusive training program that provides the benefits of classroom training at your own pace with a validity of one (1) year.
- + 20% reduction on the first year subscription for our all-in-one ISMS/GRC management solution
Official ECC-Reseller-Certificate
What is the CTIA program
EC-Council Certified Encryption Specialist (E|CES) program is designed to introduce professionals and students to the intricate field of cryptography. Covering a broad spectrum of topics, the E|CES course delves into modern symmetric key cryptography, offering detailed insights into algorithms like Feistel Functions, DES, and AES.
Additionally, students gain familiarity with various other algorithms, including Blowfish, Twofish, Skipjack, CAST, TEA, and more. The curriculum extends to information theory basics as applied to cryptography, covering essential concepts such as hashing algorithms (MD5, MD6, SHA, GOST, RIPMD 256) and asymmetric cryptography with in-depth discussions on RSA, Elgamal, Elliptic Curve, and Digital Signature Algorithm (DSA). Throughout the program, students delve into crucial cryptographic principles like diffusion, confusion, and Kerckhoff’s principle.
Practical application is emphasized, enabling students to work with cryptographic algorithms from classical ciphers like the Caesar cipher to contemporary methods such as AES and RSA. Beyond theory, the course equips students with hands-on experience setting up a VPN, encrypting a drive, and exploring steganography. Furthermore, E|CES provides practical cryptanalysis and quantum computing knowledge, ensuring a comprehensive understanding of traditional and cutting-edge cryptographic concepts. Completing the E|CES program empowers individuals to make informed decisions in selecting suitable encryption standards for their organizations.
Candidates learn the theoretical aspects of cryptography and possess the practical skills necessary for effective technology deployment. This includes the ability to implement encryption techniques, secure data with VPNs, and navigate the complexities of emerging technologies like quantum computing, making them valuable assets in cybersecurity.
Who should take this course?
- Cryptography Engineer
- Cryptography Analyst
- Cryptography Consultant
- Cryptography Auditor
- Cryptography Instructor
- Cryptography Researcher
- Signals Analyst
- Security Engineer
- Investigation Specialist
- Cryptography Security and Research Consultant
- Client Software Engineer, Security & Cryptography
- IT Security Administrator
- Cryptographer
- Compliance Analyst
- Data Security Analyst
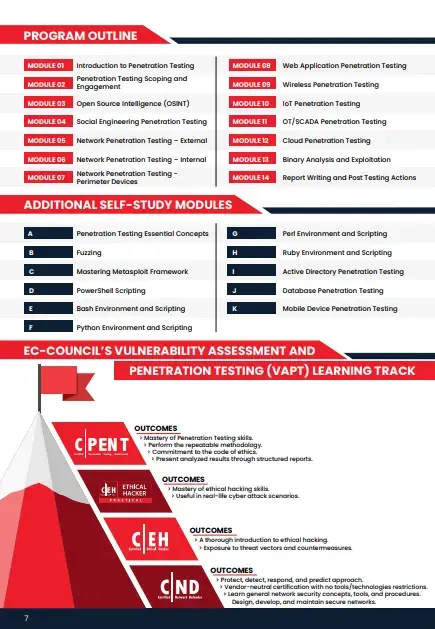
Course Outline
- Module 01: Introduction and History of Cryptography
- Module 02: Symmetric Cryptography & Hashes
- Module 03: Number Theory and Asymmetric Cryptography
- Module 04: Applications of Cryptography
- Module 05: Cryptanalysis
- Module 06: Quantum Computing and Cryptography
Achieving the CEH Certification Credential
Exam Title: Certified Threat Intelligence Analyst
Exam Code: 312-38
Number of questions: 50
Durations: 2 hours
Availability: Online
Passing score: 70
- Live remote proctor for online ECC Exam option.

Testimonial
Stel eender welke vraag over onze producten
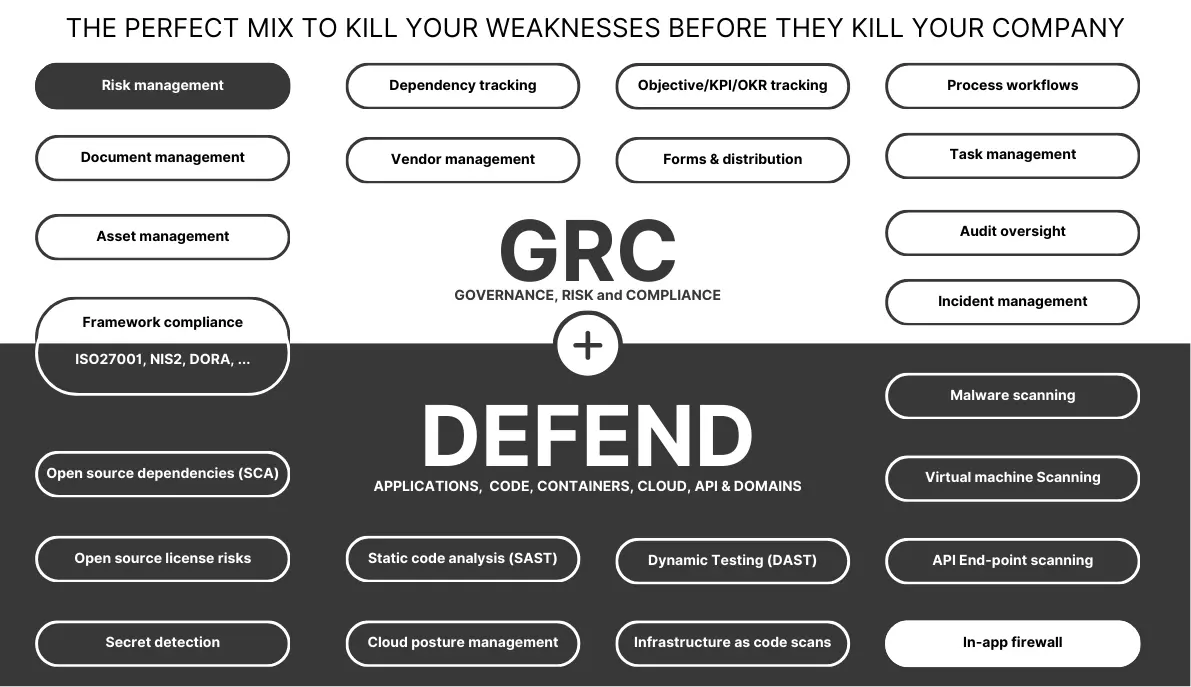
Stroomlijn uw GRC-werk met onze alles-in-één managementoplossing en krijg toegang tot ons netwerk van lokale specialisten
Start je gratis account
%20v3?unique=4144788)